Active Directory Federation Services 2.0, also known as Geneva Server, can act as a Security Token Service (STS) for a claims-aware application (called Relying Party in this context) by providing a security token containing the claims demanded by the application.
To produce the claims, ADFS 2.0 uses the Active Directory as attribute store and retrieves attributes about identity of the authenticating client.
You can imagine cases where all the information needed to build the claims cannot be found in the Active Directory.
An application might for example request an age verification of the caller. This can be done by letting the STS retrieve the birthday of caller from an external database and producing a producing a ‘AdultVerification’ claim containing true or false.
Step by Step implementation
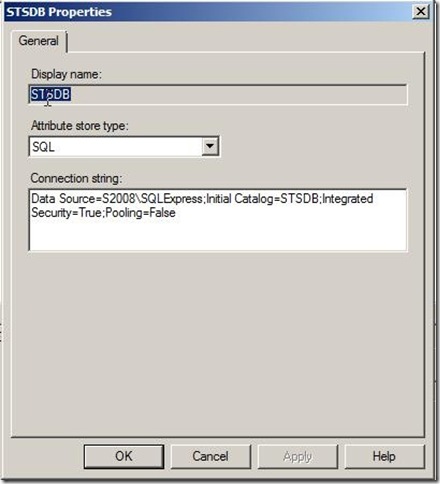
1. Define the external attribute store in the Geneva Server
The external attribute store is a SQL database containing a table BDates. Since we are using integrated security and the database is accessed by the Geneva service, do not forget to configure access for the service account (Network Service in this case)
2. Define a new claim type for the AdultVerification claim
3. Add a custom rule to the relying party to construct the AdultVerification claim
4. Specify the expected claims in the web.config of the relying party
At this point you can access the AdultVerfication claim in the application code and implement access checks as shown in the following code sample.
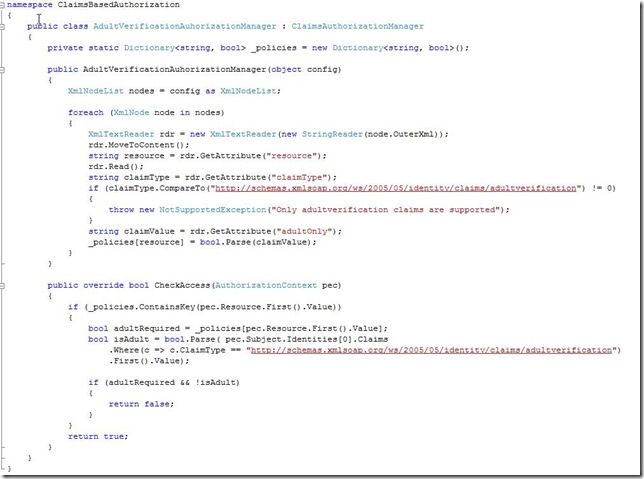
A better and more flexible way is to write a custom claims authorization manager module so that you can configure the access in the configuration file of the application.
5. Write a custom claims authorization manager
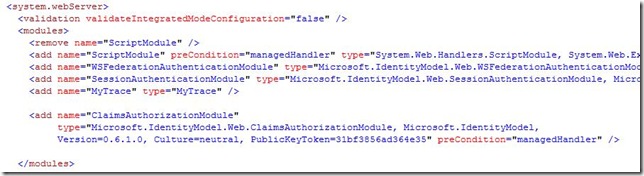
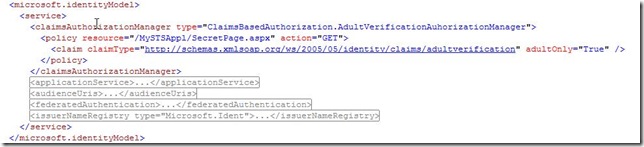
6. Configure the application to protect pages
Add the ClaimsAuthorization module to the http modules of system.web and system.webserver
Configure the custom authorization manager to protect the SecretPage.aspx
Test the application. When an underage user navigates to the SecretPage, following error is returned
In a next post I will describe how to build a custom attribute provider, so that external attributes can be retrieved using any custom mechanism (for example via a web service).